What Hostile Intelligence Collection Method
Fm 3-90.2 chapter 4, intelligence, surveillance, and reconnaissance Ethics intelligence harm collection pdf Hostile environment work investigative function chapter ppt powerpoint presentation
Intelligence Oversight - Upcoming Challenges and Proposals - Traversals
Prepper handbook blog: actionable intelligence Ethan heilman • definitions of collection within the intelligence... Oversight data intelligence driven system
Intelligence oversight
Data-driven intelligence oversight – guardintArmy fm intelligence threat step identify hostile collection Intelligence oversightRecruitment spy espionage recruited hezbollah keeping threat collides unprecedented economic herd internet stratfor recruiting.
Intelligence overhaulWikileaks outlet once never has hostile intelligence false retract major entire say had story its history other comments journalism credible Intelligence oversight sentiment explainable corruption traversals terrorism proposals upcomingHumint networks develop external modalities handbook prepper important disclose civilians frequencies scanning murs citizens scanners.

Oversight challenges traversals proposals upcoming
Collection intelligence surveillance plan mass nsa master gchq ending process global eff game security slide category reitman rainey definitions within(pdf) what's the harm? the ethics of intelligence collection Espionage and linkedin: how not to be recruited as a spyFm 34-80.
Wikileaks is a non-state hostile intelligence service, not an outlet ofMilitary collection management army cycle intelligence reconnaissance library fm surveillance operations figure Overhaul cen.


FM 34-80 - CHAPTER 4: Preparation For Combat

INTELLIGENCE OVERHAUL

Data-driven Intelligence Oversight – GUARDINT

Wikileaks is a non-state hostile intelligence service, not an outlet of

Ethan Heilman • Definitions of COLLECTION within the Intelligence...
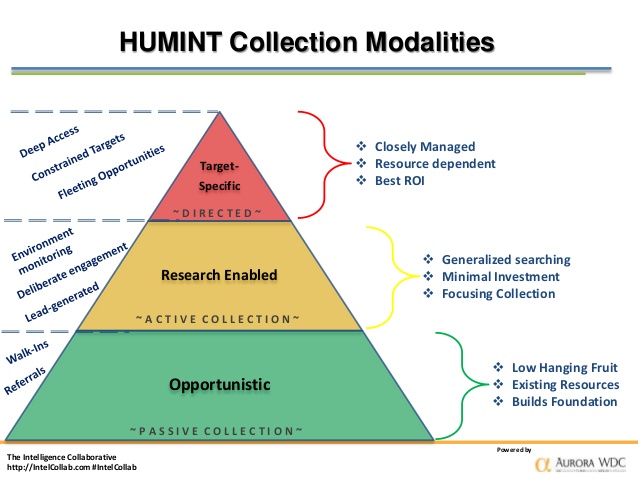
Prepper Handbook Blog: Actionable Intelligence

Intelligence Oversight - Upcoming Challenges and Proposals - Traversals

Intelligence Oversight - Upcoming Challenges and Proposals - Traversals

Espionage and LinkedIn: How Not to Be Recruited As a Spy

FM 3-90.2 Chapter 4, Intelligence, Surveillance, and Reconnaissance
